OPS201 - Introduction to Operating Systems
Contents
What is an Operating System?
An operating system (OS) does exactly what the name states: It is software that operates a computer system!
Not all computers have had or required an operating system. Particularly simple computers, including the earliest models of both business computers and microcomputers, as well as very simple embedded computers, do not require an operating system. The computer embedded into a simple mass-market microwave oven, for example, only ever runs one program, does not have communications capabilities, does not multitask, and is nevery updated, and therefore has no operating system.
However, virtually all contemporary computer systems, including embedded devices, are sufficiently complex that they are equipped with an operating system.
What does an Operating System do?
An operating system performs four main functions:
Management and Separation of Resources
Think of the specifications that were advertised when you bought your last computer (or smartphone):
- multiple CPU cores
- several gigabytes of memory (RAM)
- storage in the gigabytes-to-terabytes range
- a display with a particular resolution
- various peripherals, such as cameras, speakers, and so forth
All of these are system resources. The operating system manages these resources to ensure that they are used effectively, and to ensure that there are no conflicts over their use.
As requested by the user(s), or as triggered by other factors such as the time of day or operational requirements, the OS will create processes -- running copies of computer programs. Each process is allocated compute resources by being permitted to run on one or more computer cores. To run a large number of processes, the OS will switch between them, stopping one process and starting another as needed to ensure that all of the processes get a fair share of system resources (which may not always be an equal share).
The operating system will allocate the available memory to processes and to the operating system's internal operations. The OS will program the system hardware to ensure that no process can overwrite memory allocated to another process.
The OS will also allocate storage space to various files as they are created and extended, and deallocate space when those files are truncated (shortened) or deleted. The space allocated to one file will be protected from use in other files.
Display space is similarly shared; the operating system will ensure that multiple programs can each display in their own windows, but prevent them from destroying graphics being displayed by other windows.
Peripheral devices are managed in different ways according to the characteristics of the device. For example, sound output from multiple processes will be combined for simultaneous output to the speakers (or other output devices). However, when a process accesses a printer, output from that processes is collected into a document, and the documents are queued for sequential printing, because simultaneous access would result in garbled output.
Security Enforcement
It’s important to keep information private in some contexts, and to share information in other contexts. The operating system is responsible for enforcing security rules. For example, on a smartphone, a social media app shouldn’t be able to access data from a banking app, and on a cloud server, one customer shouldn’t be able to access another customer’s data. However, multiple smartphone apps might be permitted to access a photo album, and a company employee might need to view a report generated on a server from multiple customers’ data.
The operating system is responsible for enforcing the security rules but not for creating them -- the system administrators and/or users are responsible for creating and maintaining the security settings and policies which the operating system enforces.
Hardware Abstraction
There are many different types of devices that perform similar functions, and multiple ways that these devices can be connected. For example:
- A keyboard may be connected via a USB connection or a wireless Bluetooth connection, or may be created as a virtual keyboard on a touchscreen.
- A mouse may be connected via a wired USB, wireless USB dongle, or wireless Bluetooth connection. But there are also other types of devices which can provide the same capability of allowing the user to interact with the display, including trackpads, trackballs, and touchscreens.
- Sound may be played over built-in speakers, an external analog speaker, an analog headset, a digital speaker or headset with a USB connection, a Bluetooth speaker, earbuds, or headset, or played through a television connected via HDMI.
The operating system abstracts away these hardware details. This means that programs can access devices in a general way without having to be programmed to individually deal with each type of device that may be used. This enables a program to request keyboard input or play sounds without regard to the details of the specific hardware available.
Maintaining the Programming Model
The operating system, computer hardware, and development tools (compiler, linker, and so forth) work together to present the “programming model” – a conceptual framework which software developers use when creating software. For example, several different application program may be designed to occupy the same area of memory; obviously, this presents a conflict when these applications are used at the same time, so the operating system works with the computer’s hardware to load the applications into different areas of physical memory, and then use the computer’s virtual memory capabilities to make each program appear to be loaded into the region of memory for which it was written.
Components of an Operating System
Most modern operating systems are delivered as five separate and inter-related parts:
The Kernel
This is the heart of the operating system, the main program (or group of programs) that controls the computer. The kernel operates in a special privileged mode, which allows it to manage the resources and security settings for all other software. The kernel is loaded by the computer’s firmware (built-in software) and sets up the computer’s hardware and resources before starting the services and user interface(s) in non-privileged mode, programming the computer’s hardware to enforce the privilege level.
System Libraries
Many programs need to perform the same operations, such as accessing the network, playing sound, or drawing something on the screen. Libraries provide a common set of software routines (also known as functions, methods, procedures, or subroutines) which programs access to perform these common operations. This eliminates the need for each program to contain duplicate code for these common operations, which reduces software duplication and program size. Although additional libraries may be installed on the computer, the system libraries provided as part of the operating system provide the most broadly-used routines required by nearly every program.
Services
These are programs that run continuously in the background, providing services such as WiFi authentication, print management, and file sharing. Unlike the kernel, these programs don’t operate with full system privilege, and are therefore subject to the same type of resource and security management as regular programs, and they also utilize the system libraries.
The User Interface(s)
This is the software that enables the user to interact with the system. Most operating systems provide at least two user interfaces:
1. A text-based user interface that enables the user to enter commands, view the output from those commands, and interact with full-screen text interfaces such as file editors and file managers. This may be referred to as a text user interface (TUI) or a command line interface (CLI).
2. A graphical user interface (GUI) that typically enables the user to interact with multiple application windows, using a keyboard and a pointing device such as a mouse, trackpad, or touchscreen.
Utilities and Applications
Most operating systems provide a set of tools to enable users to perform setup, configuration, and maintenance tasks. For example, they may provide “utility” software to add/remove software, configure hardware, and manage files. This utility software may take the form of commands that are accessed through a CLI, or graphical utilities that are accessed through a GUI. Most operating systems also provide a set of basic starter applications, such as a text editor, clock, a few games, and sometimes a web browser; the quantity and complexity of the included applications vary considerably from one operating system to another.
GUI vs CLI: Advantages and Disadvantages
Both graphical user interfaces (GUIs) and Command Line Interfaces (CLIs) have strengths and weaknesses, making them suited for different types of use.
The visual nature of a graphical user interface makes it well-suited for creating, editing, and viewing visual media, such as photos, videos, presentations, and highly-formatted documents. A GUI is also well-suited to dense displays of visual information, such as data dashboards. However, most GUIs are not well-suited to automation, and the large amount of information in the display may consume a lot of network bandwidth if the GUI is used over a remote connection.
On the other hand, a CLI is well-suited to task automation, and many tasks may require fewer steps to perform than when using a GUI. CLIs generall require much less bandwidth when used over a network, making them well-suited to remote administration tasks.
To compare the data demands of the two types of user interfaces:
- A GUI on a 1920x1080 ("full high definition") monitor displays about 6 megabytes of data (2 million pixels x 3 bytes per pixel)
- A TUI on an 80x25 character terminal displays about 2 kilobytes of data (0.002 megabytes) at one time
As an example of the strengths of each type of user interface, consider the task of croping, resizing, and changing the format of photographs:
- A GUI immediately shows the effect of changes and allows the adjustments to be easily fine-tuned, producing exact results for a small number of photos. However, it may take many steps to perform the edits, so editing hundreds of photographs will take a very long time.
- A CLI is well-suited to automation. Edits could be applied to hundreds of pictures in a few seconds, if the edits can be adequately described on the command-line.
A Brief History of Operating Systems
Many operating systems have been released. This is a timeline of some of the milestone events leading to some of the most prominent operating systems used today:
- Before the mid-1960s: A number of different manufacturers produced various computers for business. Since these machines were expensive, and because there were many different manufacturers, a relatively small number of machines of each model were produced. Very little was standardized, and data was rarely interchanged between computers. Consequently, there were many different operating systems, each with a fairly small market.
- 1964/1965 - MIT and partners begin the Multics Project. This project introduced many concepts that became common in later operating systems, including a heirarcical filesystem, multitasking, and interactive operation. This project continued through 2000. However, Multics was a fairly resource-intensive operating system and ran only on very specific hardare.
- 1969 - Bell Labs decided to end their participation in the Multics project. Dennis Ritchie and Ken Thompson, Bell Labs employees who were familiar with the Multics project, decided to implement some of its features in a much lighter-weight operating system, which they called Unix. Unix was soon rewritten in the C language, and could be fairly easily ported to other types of computers.
- 1970s - Unix continued to grow in popularity. Many computer vendors licensed it and adapted it to work with their computers; some of these variants included Xenix (Microsoft), AIX (IBM), Ultrix (Digital Equipment Corporation), HP/UX (HP), and many others.
- 1976 - Microcomputers, 8-bit computers inexpensive enough to be purchased by individuals or small businesses, became widely available. Digital Research's CP/M operating system became popular on Intel- and Zilog-based microcomputers.
- 1981 - IBM decided to enter the microcomputer market with the IBM PC. Needing an operating system, IBM contacted Microsoft - but their only operating system at the time was Xenix, and the IBM PC was not powerful enough to run Xenix well, so Microsoft licensed (and later purchased) a CP/M clone named 86/DOS (aka QDOS) from a local computer company (Seattle Computer Products). This operating system was used as the basis for Microsoft's DOS (disk operating system) product, named PC/DOS when marketed by IBM or MS/DOS when marketed by Microsoft.
- 1983 - The IBM PC was successful in the market, due to both IBM's marketing and the fact that IBM published the technical specifications which enabled other companies to sell compatible accessories, so IBM produced more powerful models including the IBM PC/XT (1983) and PC/AT (1984). These models had much larger amounts of RAM as well as hard disks, so Microsoft needed to update DOS with new features; they did this by incorporating some features from Xenix (their Unix version), including a heirarchical filesystem.
- 1984 - Richard Stallman created GNU Project and the Free Software Foundation to promote the concept of Free Software ("free" in the sense of freedom, not free of cost).
- 1984 - The X Window System is first developed at MIT to provide a cross-platform foundation for graphical user interfaces. It becomes widely used on Unix systems sold by many different vendors.
- 1985 - Microsoft introduced Windows 1.0, which was used in conjuction with DOS. Windows provided a graphical user interface and multitasking (though both were initially very limited).
- 1991 - Linux Torvalds, a computer science student in Finland, wrote and released the Linux kernel. The Linux kernel, combined with software from the GNU project and other free software projects such as the X Window System, made a useful operating system (often referred to as "GNU/Linux" or just "Linux").
- 1992 - IBM and Microsoft ended their collaboration on OS/2, an advanced operating system with a graphical user interface. IBM continued independent development of OS/2.
- 1993 - Microsoft introduced Windows/NT (for "New Technology"), incorporating some concepts from OS/2. Unlike previous versions of Windows which required DOS, Windows/NT provided a complete (and more advanced) operating system with a GUI and did not require DOS. All future versions of Windows were based on Windows/NT.
- 2001 - Apple released MacOS, a Unix-like operating system based on the "Darwin" kernel
- 2007 - A consortium of developers called the Open Handset Alliance, led by Google, released the Android operating system for mobile devices. The Android platform is based on the Linux kernel.
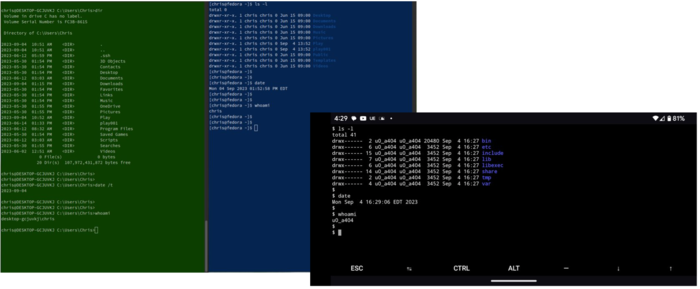
Anatomy of a Command Line Interface (CLI)
A CLI is provided by two programs:
- A terminal program, which is responsible for collecting user input and displaying the output from the shell and commands.
- A shell, which interprets the user's written commands.
These may be on the same machine, or they may be on different computers. For example, it is common to access both Linux and Windows systems over a remote connection, using a protocol such as SSH (secure shell). In that case, the terminal program runs on the computer in front of the user, and the shell runs on the remote computer system.